Proactive cybersecurity measures vs. reactive tactics
Threats in the cybersecurity ecosystem are evolving at an unprecedented pace, and simply reacting to attacks leaves businesses vulnerable.
While traditional security approaches focus on mitigating damage once a security incident has occurred (reactive tactics), adopting proactive cybersecurity measures allows organizations to anticipate threats, neutralizing them before they materialize in their infrastructure.
Companies that rely solely on reactive security measures risk suffering major negative impacts, including financial losses, reputational damage, and operational disruptions. In some cases, the damage can be irreparable due to poor backup management.

What is proactive cybersecurity?
Proactive cybersecurity aims to prevent and anticipate incidents before they happen. It involves continuous monitoring, vulnerability assessments, and predictive analysis to detect potential risks early.
This approach is crucial for mitigating sophisticated threats and reducing risks through greater control over systems and security posture. As cybercriminals continue to develop new tactics, techniques, and procedures (TTPs) to bypass security defenses, a proactive strategy becomes even more critical.
Key components of proactive cybersecurity
- Threat intelligence & threat mapping – The main focus is on identifying potential risks before they can be exploited.
- Penetration testing & red team exercises – Simulations of cyberattacks help uncover security gaps.
- Continuous security monitoring – There is 24/7 surveillance to detect anomalies in real time.
- Zero trust architecture – A special security model that ensures strict access control and continuous verification.
- AI-driven risk analysis – The use of machine learning helps to predict and prevent cyber threats.
Organizations prioritizing proactive security measures are better equipped to defend against increasingly sophisticated cyber threats. These are some of the advantages of a proactive cybersecurity approach:
- It reduces the risk of successful cyberattacks.
- It minimizes financial losses by preventing security breaches.
- It enhances compliance with regulatory requirements.
- It strengthens overall security posture and business continuity.
What is reactive cybersecurity?
Reactive cybersecurity, on the other hand, focuses on responding to security incidents after they have already impacted an organization. Its primary objectives include mitigating the damage caused by an attack and restoring affected systems as quickly as possible.
While essential, relying solely on reactive measures leaves organizations vulnerable to constantly evolving attack techniques.
Key components of reactive cybersecurity
- Incident response plans – Creation of frameworks for containing and mitigating cyberattacks once they occur.
- Forensic analysis – After the attack, investigating the source and impact of the breaches to prevent recurrence.
- Disaster recovery & backup management – Focusing on restoring lost data and resuming operations post-attack.
- Security patching – Addressing vulnerabilities after they have been exploited.
Reactive security is essential for handling incidents. However, it:
- leaves organizations exposed until an attack is detected.
- increases the likelihood of financial and reputational damage.
- often results in higher long-term costs due to recovery expenses.
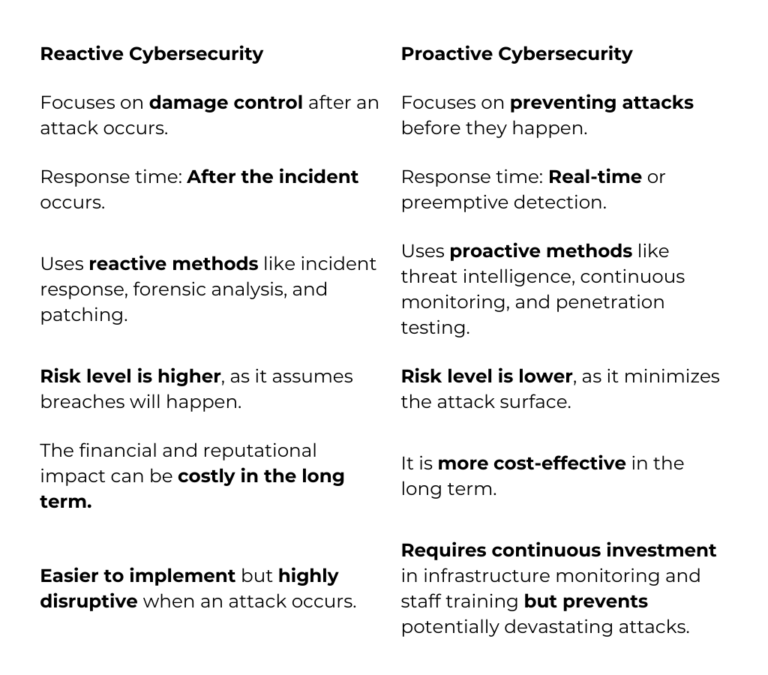
Comparing reactive vs. proactive cybersecurity approaches
Why organizations need proactive cybersecurity
Investing in proactive cybersecurity measures helps organizations mitigate risks while improving overall resilience and compliance with regulations.
- Regulatory compliance requires it – Regulations such as GDPR and NIS2 mandate stricter security postures, often necessitating proactive defenses.
- The financial impact of breaches is rising – The cost of cybersecurity incidents continues to increase, making prevention more cost-effective than recovery.
- Reputation is a critical asset – Trust is key, and a single breach can erode customer confidence, harming long-term business viability.
- Cybercrime is becoming more advanced – The rise of AI-powered attacks and ransomware-as-a-service (RaaS) is making traditional security strategies ineffective.
- Operational continuity relies on prevention – Cyberattacks can disrupt critical business operations, leading to downtime and loss of productivity.
How Clovr Labs implements proactive security
At Clovr Labs, we believe cybersecurity should stay one step ahead, not one step behind. Our proactive security approach includes:
- AI-powered threat detection – Leveraging machine learning to identify anomalies and detect threats in real time.
- Advanced threat mapping & vulnerability assessments – Identifying security gaps before they can be exploited.
- Penetration testing and red teaming – Simulating attacks to discover vulnerabilities before cybercriminals do.
- Continuous security monitoring – Providing 24/7 surveillance to detect and neutralize potential threats.
- Cyber awareness training – Equipping teams to recognize and prevent social engineering attacks.
- Zero Trust security models – Implementing strict access controls to minimize insider and external threats.
Proactive cybersecurity is not just about deploying the right technology—it requires a strategic, intelligence-driven approach that evolves with emerging threats.
Don’t wait for an attack to happen! Contact Clovr Labs today to assess your organization’s cyber resilience and implement a forward-thinking defense strategy.